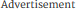Intro
Sitting at your local coffee shop you use public Wi-Fi to browse the web, pay your bills, and catch up on your social network accounts. Nothing is out of the ordinary, you do this every Saturday morning. Suddenly you get a message from your bank about a $1000 purchase that you made earlier in the day. You check your wallet, but your cards are still there. So what happened? Your identity was stolen from you while you were using their public Wi-Fi. More than likely you were a victim of a MiTM attack (Man-in-The-Middle attack). With increasing threats to the online community like MiTM attacks, knowing that your data transfers are secure can prevent your valuable information from being stolen.
Man-in-the-middle attacks
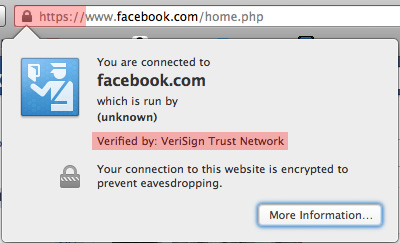
In a basic scenario, lets say you’re Bob and you’re communicating to Susan. Let’s assume you’re communicating through an unencrypted medium. Because the communication medium is unencrypted, a third person, Jack, can enter into the conversation without you knowing. Jack can now create 2 separate communications, one between you and Jack and another between Jack and Susan. But because Jack is still relaying the messages you send Susan and vice versa, you and Susan still think that you’re talking to each other; when in fact you’re both communicating through Jack. At this time Jack has taken over your identity and can send anything to Susan but Susan will think it’s still coming from you. In the example of online banking, the attacker is now recognized as the original account holder and can make transactions and changes as if they were you.
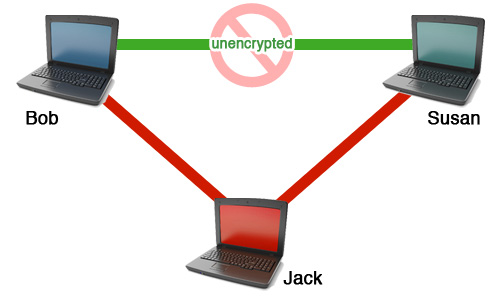
In more complex scenarios, hackers can use self-signed SSL certificates to give you the illusion of security. In this instance, hackers exploit the public key handshake that initiates secure socket layer communications. So, you may see the “https” in your browser’s URL and think you’re safe, but without verifying the validity of the SSL certificate used, it’s hard to say whether your information is truly secure.
That’s why your bank is asking if you made a $1000 purchase.
So what can you do to be safe?
HTTPS/TLS/SSL
A commonly missed/ignored system of security is something called Hypertext Transfer Protocol Secure (HTTPS). Ever noticed the http:// in-front of a link that you type? That’s Hypertext Transfer Protocol (HTTP) the standard protocol used to request communication from a website. Using regular HTTP your data isn’t encrypted hence it’s not secure and is vulnerable to attacks. https:// (HTTPS) on the other hand is encrypted; it’s HTTP layered with Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols. With HTTPS any data that you send from your computer will be encrypted with a public key and will only be decrypted once it has safely arrived at your intended location. Upon arrival, only a server that has the private key can decrypt the data and vice versa. Public keys are used to encrypt and are open to public use, while private keys are used to decrypt and are only available to authorized websites. The two keys are linked but neither key can perform both task (encrypting and decrypting), making sure that only an authorized website can decrypt your data.
So how do we know that the website we are communicating with is who they say they are?
As mentioned above, “https” appearing in the browser URL doesn’t guarantee a secure connection - just an encrypted connection. Luckily, CA’s (certificate authorities) can help your browser distinguish the difference between a trusted website - and a potentially malicious site. CA’s are third-party companies that issue digital certificates that certify that a website owns the public key that you used to encrypt your data. Most browsers are equipped with a method to view such certificates, usually by clicking an icon in-front of https:// on the URL bar. Making sure that the website you’re on is certified and secure can save you from malicious attacks.
Fully logout after each session
Another method an attacker can use to steal your identity is to steal your session information. Every time you’re on a website you’re starting a “session”, a session is basically any type of data exchange between two devices or computer (ex. you login to Facebook). Websites use session tokens to identify your current session, information that tells the website who you are. Session tokens are usually stored on the client (your computer) in the form of HTTP cookies. These cookies store your unique identification, like information saying you’re logged into your Facebook or online banking accounts. Sessions are time-based so until you fully logout your information may be available for a decent period of time. Logging out at the end of each session will ensure that you’re not subject to any malicious activities. And remember when using a public computer to never let the browser save usernames and passwords or maintain an open session.
Secure your network
Whenever possible, use your own network - but be sure that you’re set the appropriate access and security rules to ensure that no one else can interlope on your private communications. For example, you’ll want to at the very least set up encryption and a secure password (see our password generator: www.designbrooklyn.com/password-generator). If possible, it’s a great idea to limit access to specific devices using a mac address filter. It’s a little bit of an inconvenience when your friend wants to hop on your wireless, but it’s an effective measure to keep hackers out of your network.
Conclusion
- Check that you’re using HTTPS. Look for https:// in-front of their website link.
- On HTTPS websites, make sure to check the digital certificate to see that it’s signed and verified.
- If you’re using public Wi-Fi or computers remember to fully logout.
- If you’re using a public computer never let the browser save your login information.
- Unless absolutely necessary it is advisable to avoid online banking using public Wi-Fi or computers.
- Make sure that your private network is secure.
Following these guidelines is a good start to becoming more safe and secure while browsing the internet. And as always, remember to use and update your antivirus, anti-malware and firewall software.
http://www.sans.org/reading_room/whitepapers/threats/ssl-man-in-the-middle-attacks_480
How to deploy HTTPS correctly: https://www.eff.org/https-everywhere/deploying-https
IBM explains digital certificates and SSL: http://pic.dhe.ibm.com/infocenter/tivihelp/v2r1/index.jsp?topic=/com.ibm.itame2.doc_5.1/ss7aumst19.htm&path=3_6_0_6_0_5_0_4_6_3_1_1